SSO on Keycloak
Precontidions
Creat a new client in Keycloak
First we need to setup a new client.
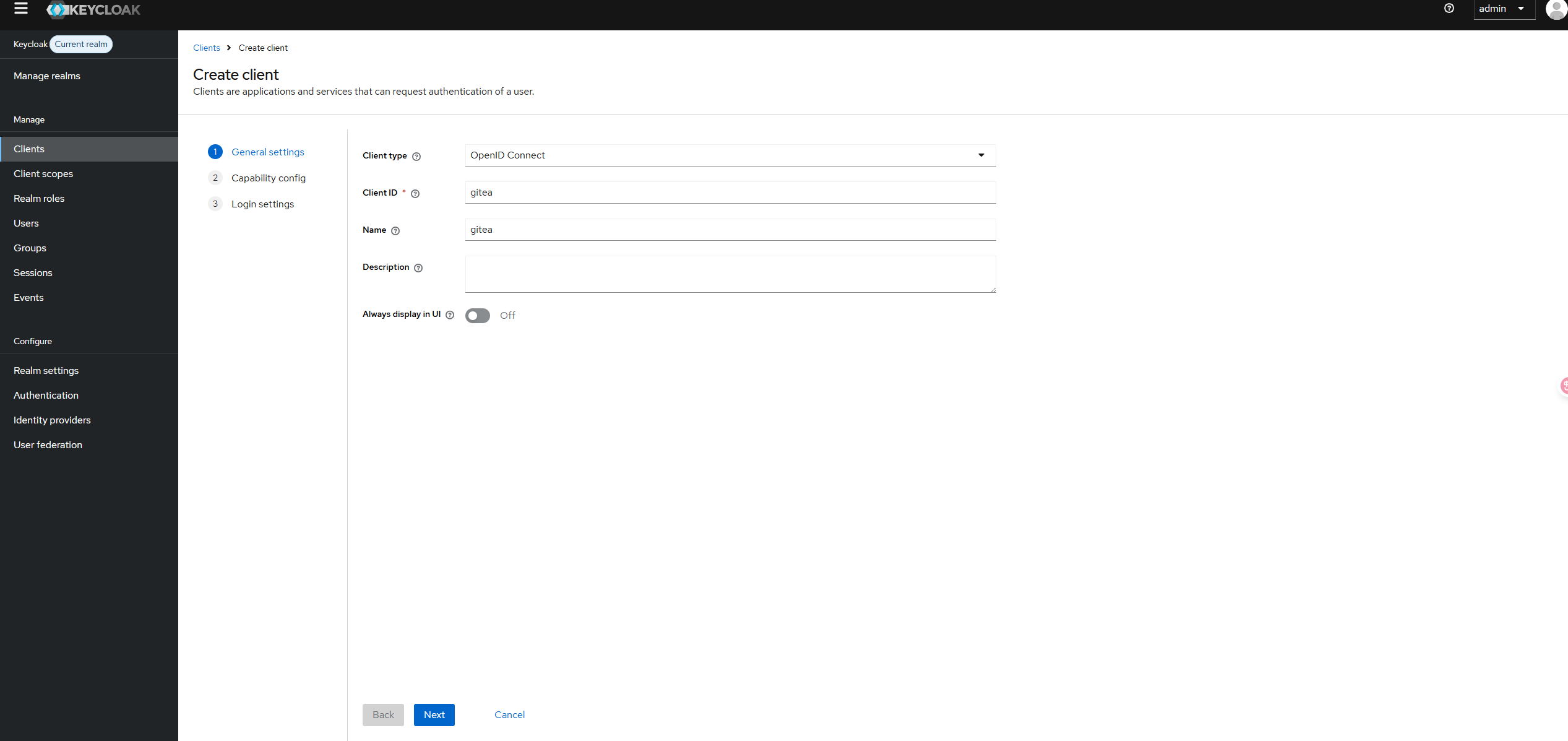
Start by logging into your keycloak server, select the realm you want to use (master by default) and then go to Clients and click the Create client button at the top.
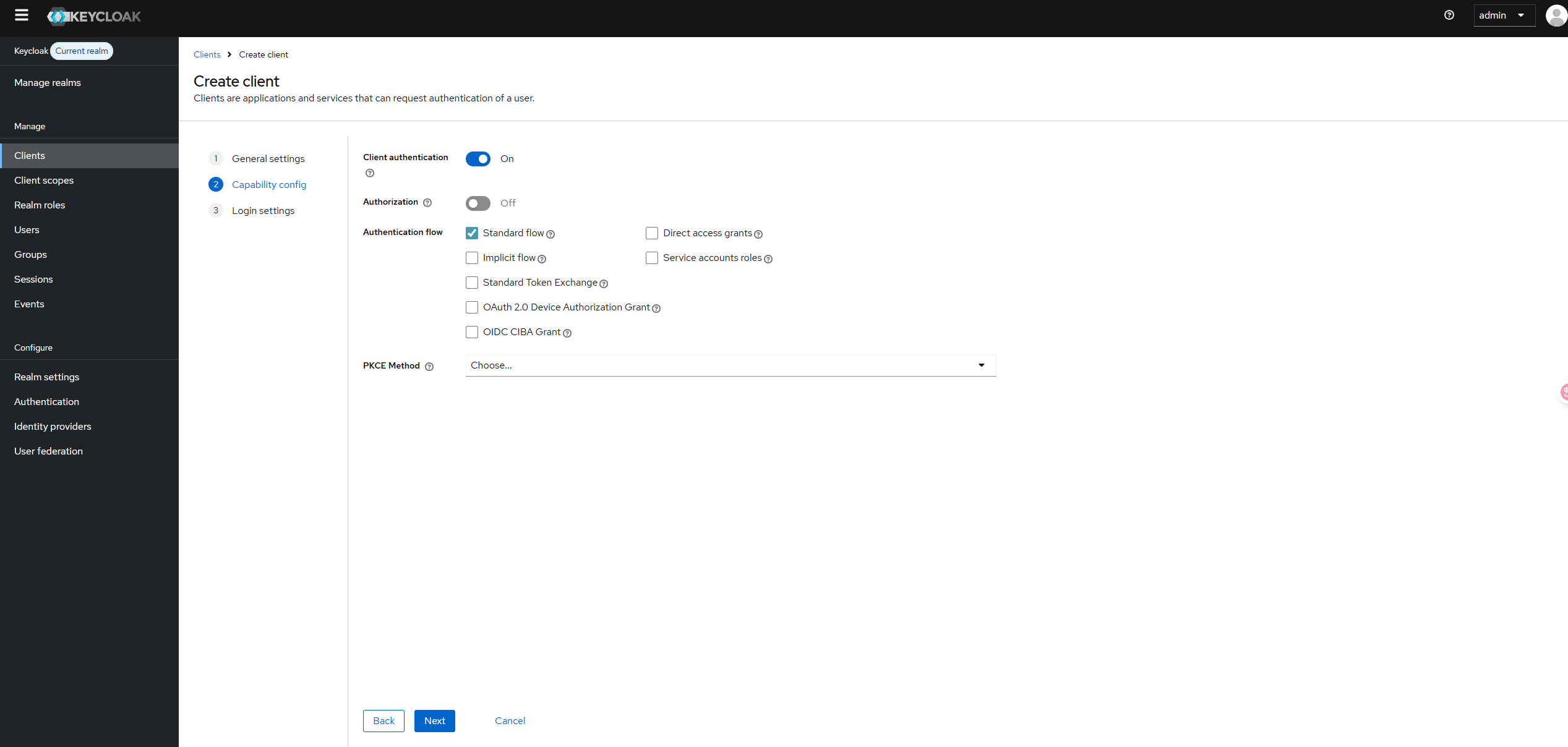
Enable the Client authentication.
Configure the client by setting the Root URL, Web origins, Admin URL to the hostname (https://{hostname}).
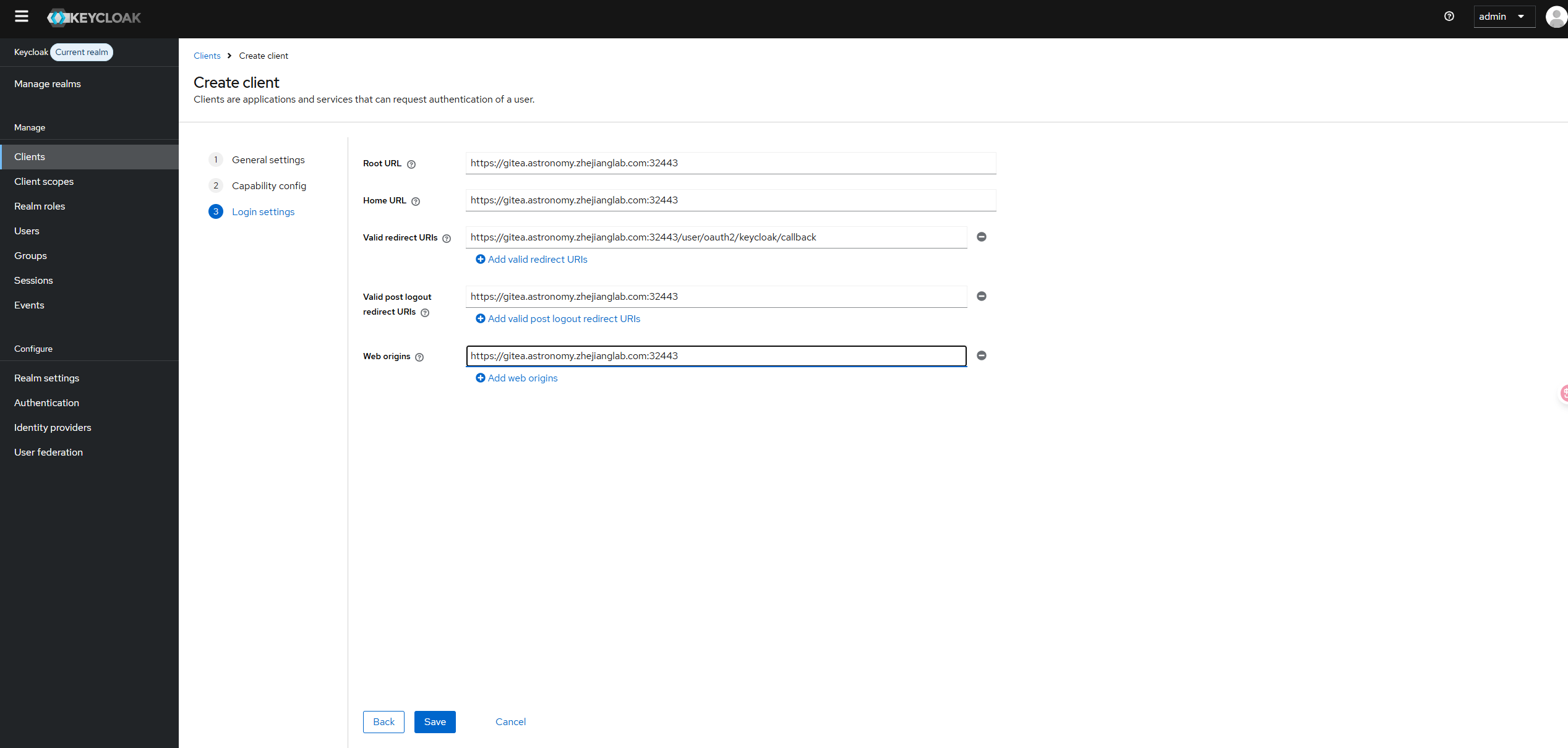
Make sure to click Save.
Add a OIDC(keycloak) auth source in gitea
- Click
Add Auth Sourcebutton onAuth Source Page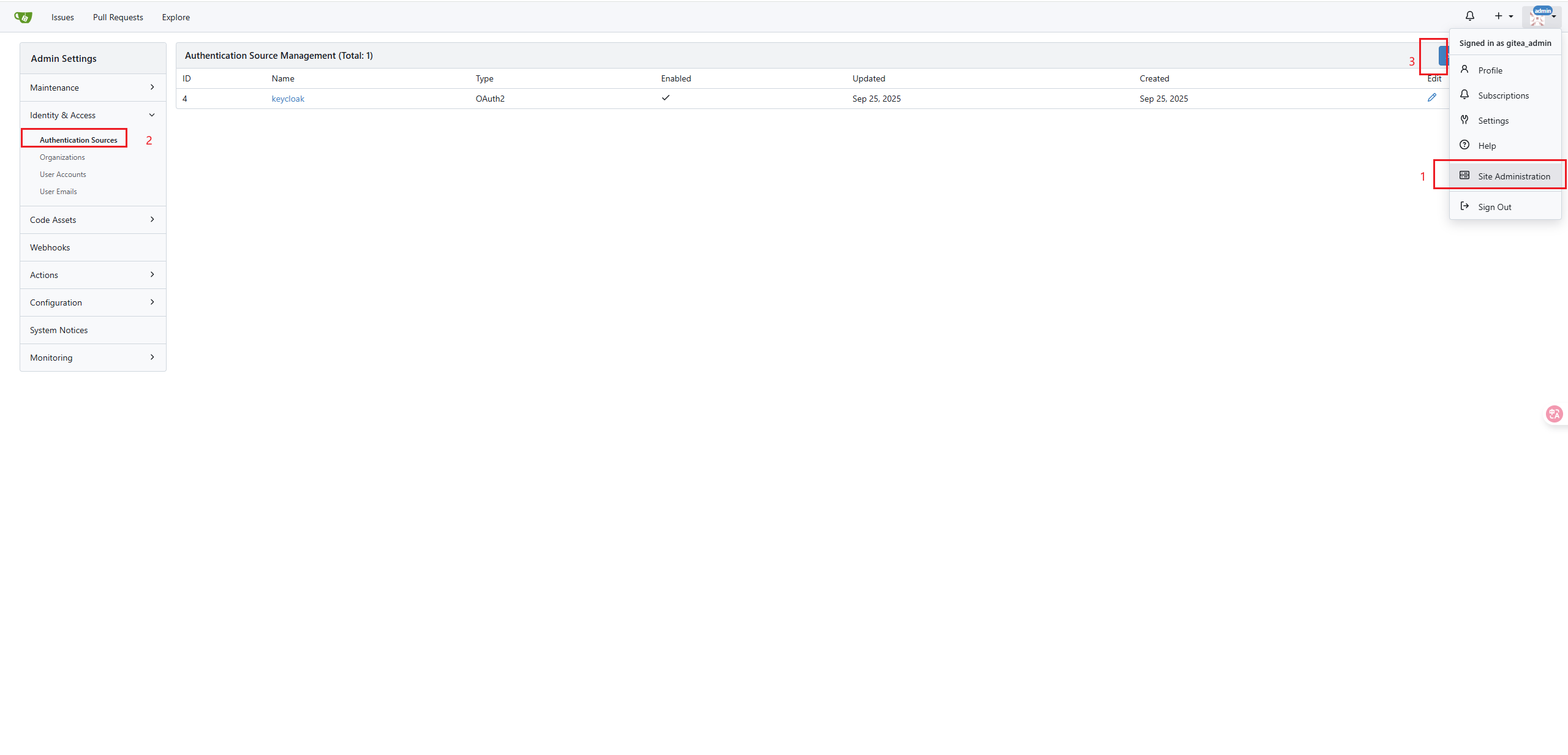
- Config the OIDC auth source
https://keycloak.astronomy.zhejianglab.com:32443/realms/master/.well-known/openid-configuration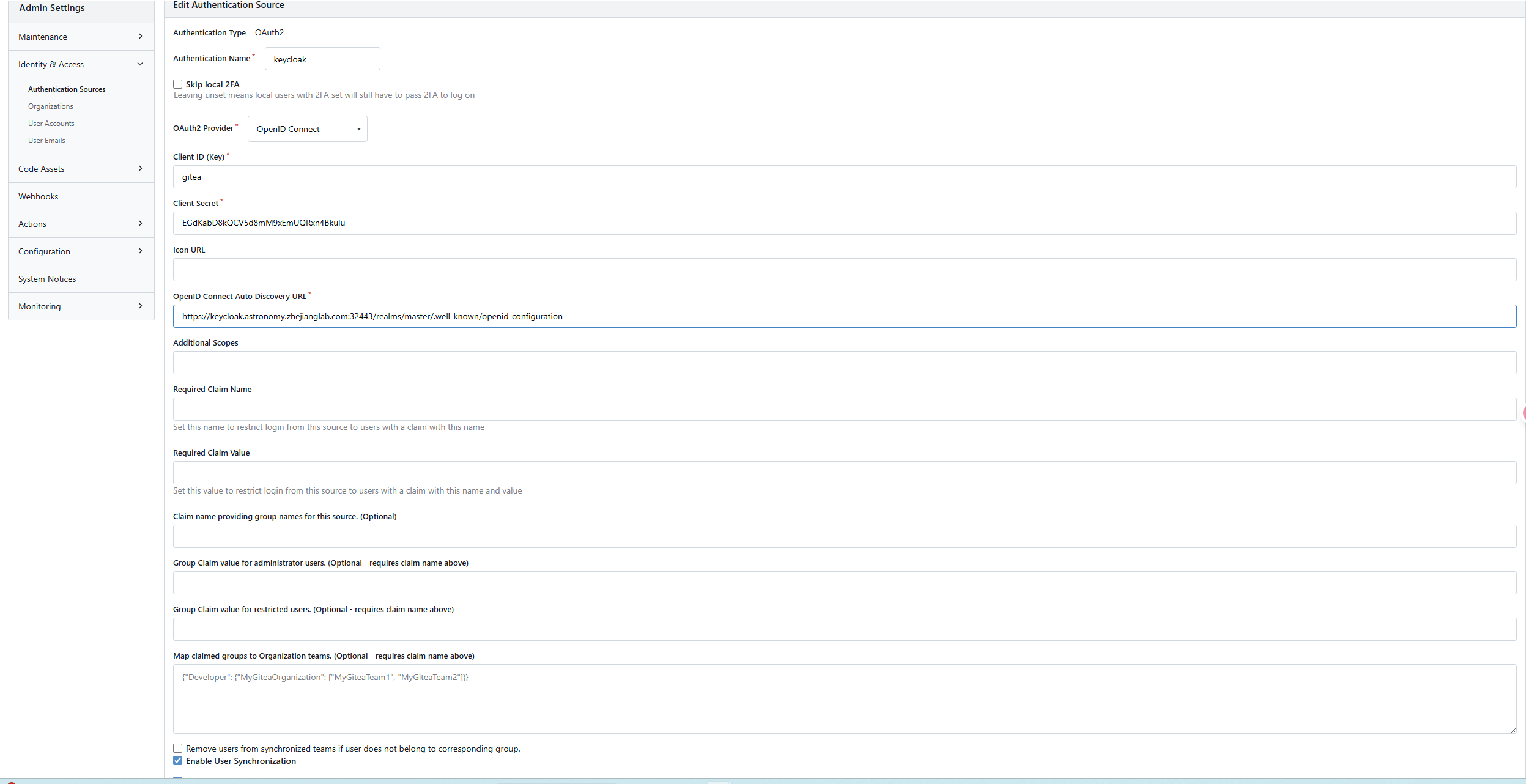
Test login
-
Use user and password from keycloak to login.
Return to the login page, and you'll find an additional "sign in with Keycloak" button.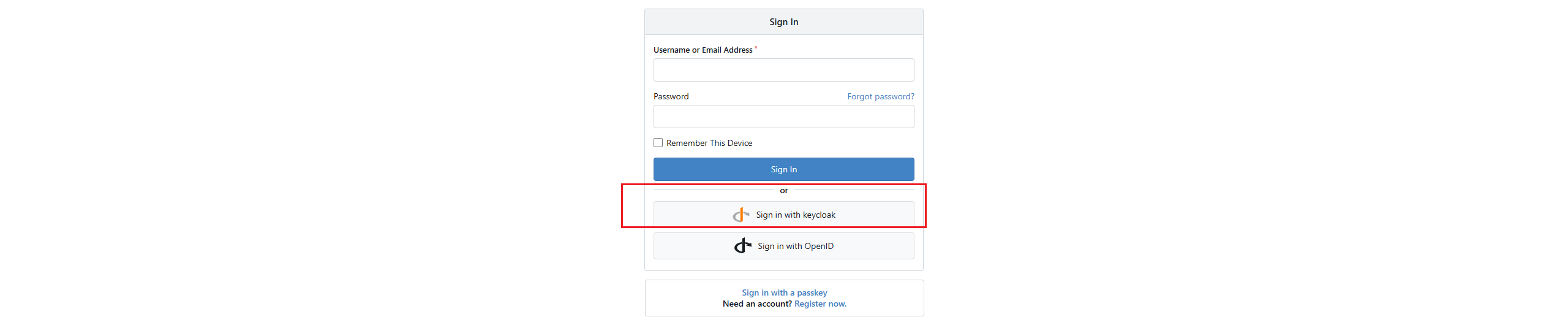
After clicking, you will be redirected to the Keycloak login page to log in using the user created in advance in Keycloak.
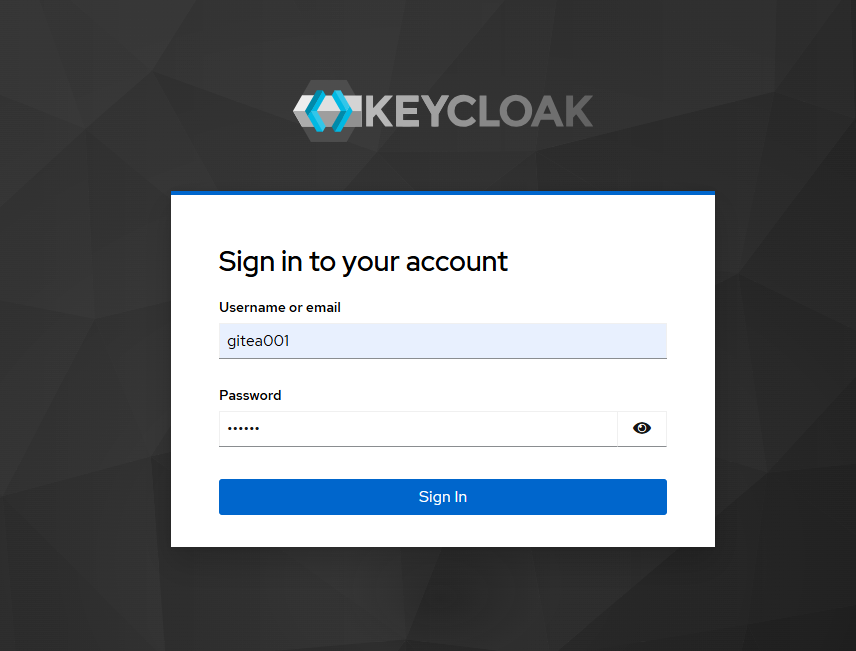
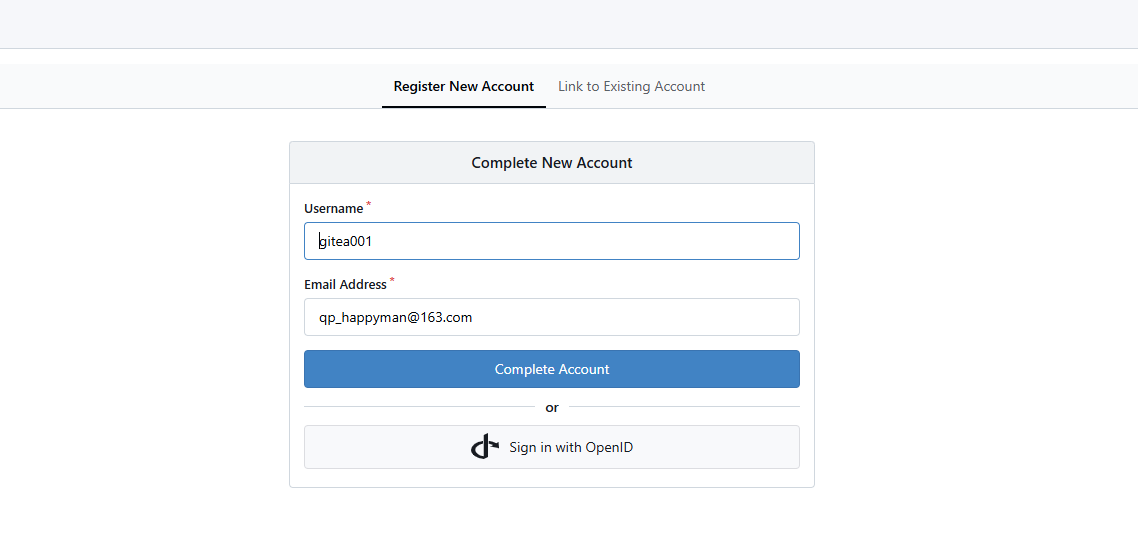
If the authentication is successful, you will be returned to the interface for registering a user account on Gitea. If the entered user does not yet exist on Gitea, registration is required in the "Register New Account" section, mainly to determine the username and email address.
infoIf the gitea configuration "oauth2_client.ENABLE_AUTO_REGISTRATION" is set to "true", there will be no this redirection, and accounts from Keycloak will be automatically registered.
 After that, you can log in normally through Keycloak.
After that, you can log in normally through Keycloak.
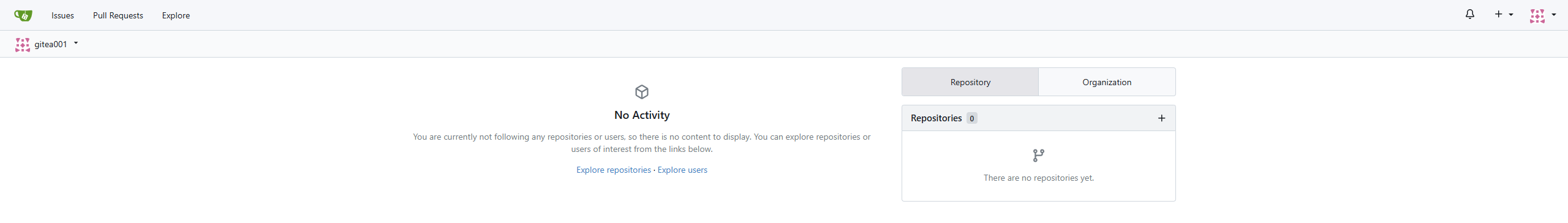
Set Gitea administrator privileges for the user
- On the Keycloak side, create a role
gitea_adminwith administrator privileges through "Realm Roles" > "Create Role"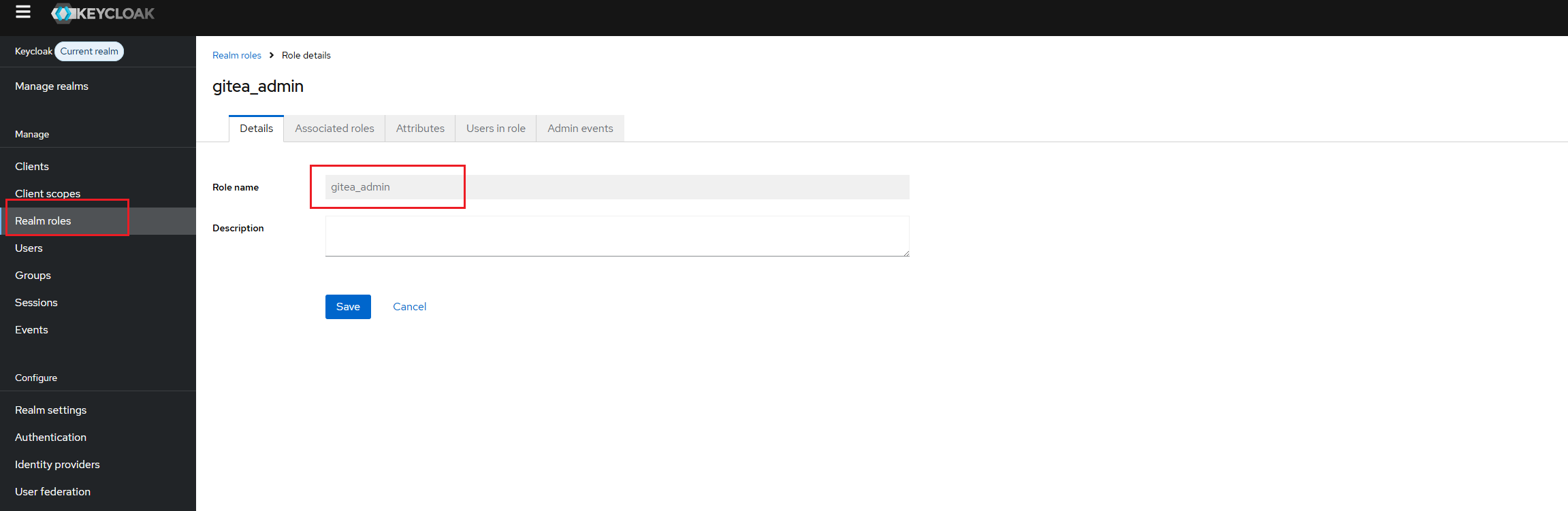
- Create a user named
gitea_admin_userand assigngitea_adminto it from the "Role Mapping" tab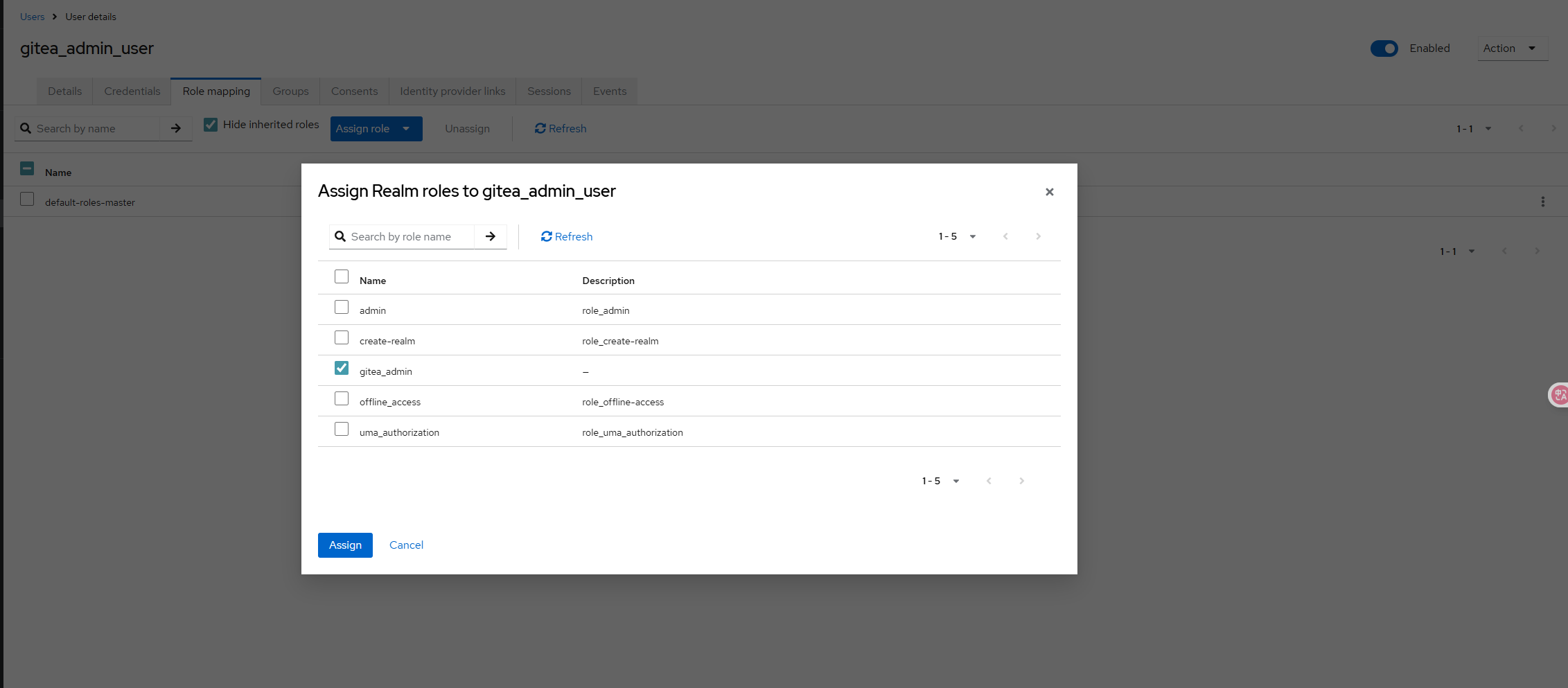
- Select "Clients" > "gitea (Client ID)" > "Client Scopes" tab > "gitea-dedicated", and Add predefined mapper, find "groups" and add
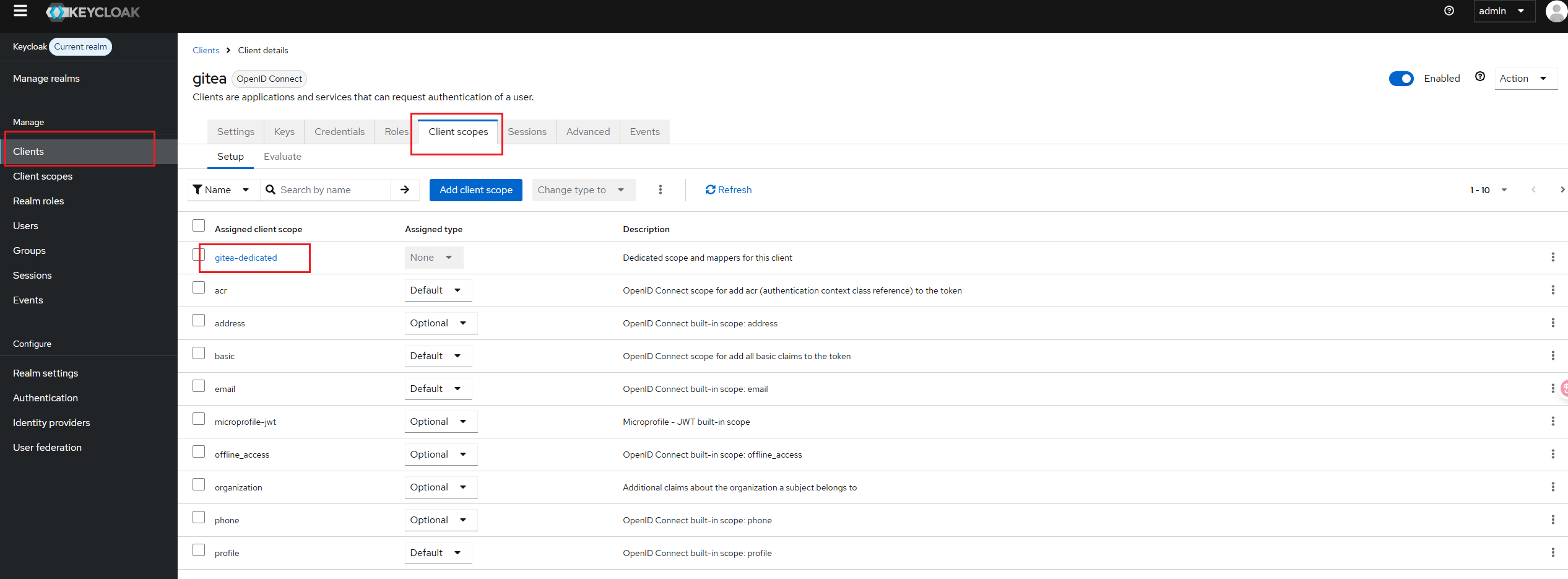
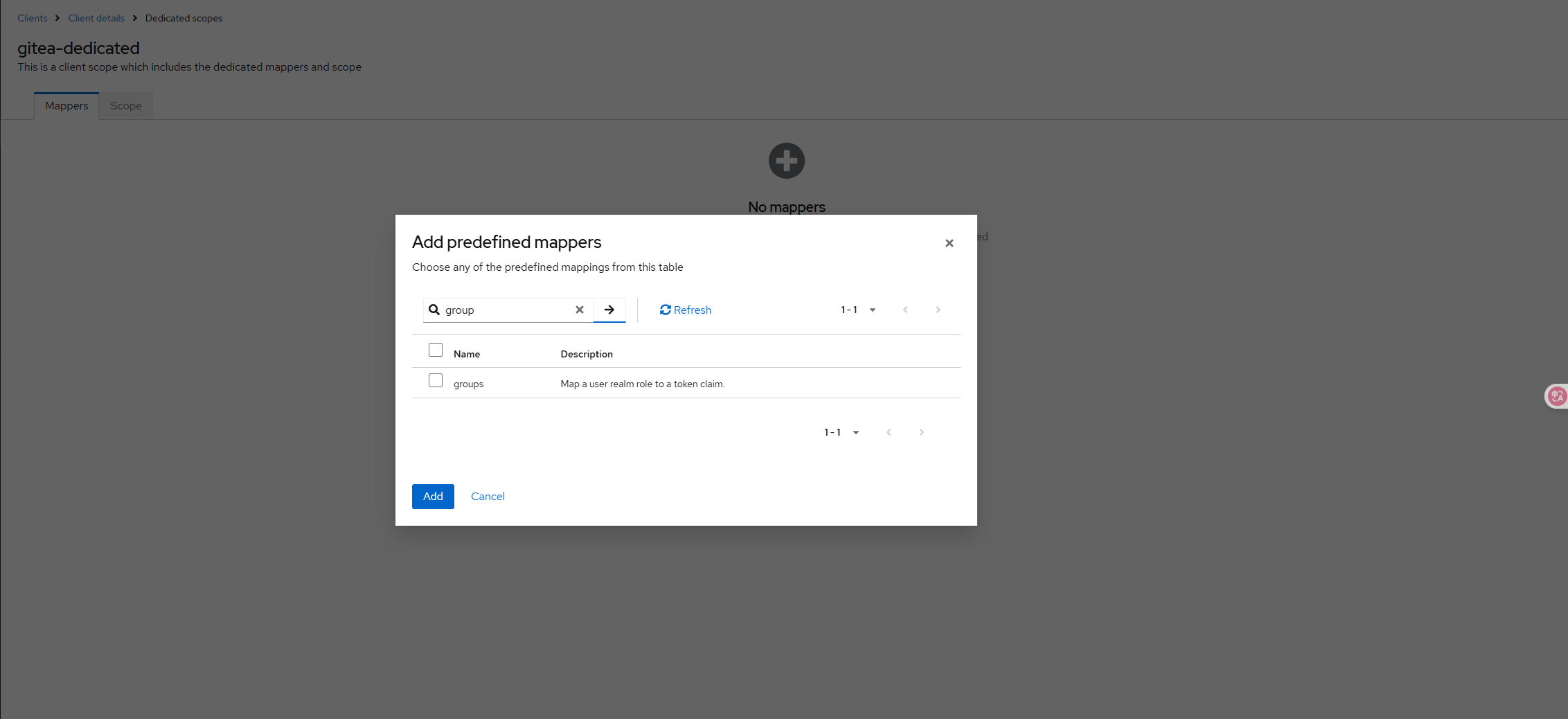
- In the Gitea configuration, edit the OIDC authentication source you previously created and add the following items
- Using the user
gitea_admin_userfor single sign-on(keycloak), you will find that this user has admin privileges